First of all, Who is Hacker??
 Hacker is the person who tries to access your computer, Online accounts like facebook, Your wifi, mobile without admin permission.
Hacker is the person who tries to access your computer, Online accounts like facebook, Your wifi, mobile without admin permission.
Also, read:
Latest 42 WhatsApp tricks for Android
Full form of Hacker
Hacker stands for
H – Hide IP
A – Aim Victim
C – Crack Encrypt
K – Kill Firewall
E – Enter into Database
R – Return Anonymous
H – Hide IP
what is IP address: IP stands for Internet protocol do not get confuse by full form basically, this is the address of your device every device (does not matter smartphone or computer) has unique IP address like mobile search on Google my IP you will find your Ip address
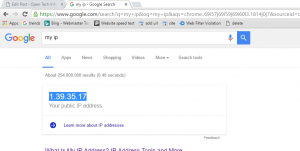
This is my public IP there are two types of IP
- Private IP
- Public IP
From a network, all device are communicating with the Internet from a single public IP address. Public IP can be same but Private IP can’t same of two or more devices.
How can you Hide IP
Hide IP address means to change or spoof your internet protocol address so sites that hacker visit to get a fake Ip address hackers can hide IP with the help of Vpn and proxy sites.
What is VPN A VPN (Virtual private network) connects two devices securely and privately over the internet through Public IP address. No one able to see I what information is exchanged.
How it works: To Understand working of VPN see this picture Here is first path without VPN here we directly connect with any site and they get our IP but when we use VPN first of all,we connect a third party server and server connected to site and site got server IP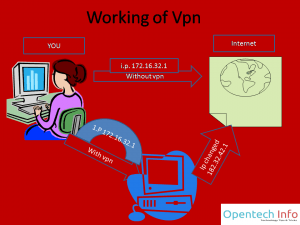
On hiding identity, no one can trace hacker so he/she will not be caught on hacking websites.
A – Aim Victim
Aim victim means if you want to hack facebook account of b then b is your victim.
C – Crack Encrypt
encrypt data means convert information into a cipher or code, especially to prevent unauthorized access. Now crack encrypt means find data that encrypt our account data(username and password) is encrypted by company hackers can use Man in Middle Attack to decrypt data
K – Kill Firewall
Firewall: These are basically parts of a computer that are used to block unauthorized access to a network. Every college wifi uses a firewall to block sites. Now kill firewall mean that access blocked content.
Read: How to hack wifi
E – Enter into Database
Database: basically this is a structured data on a computer, especially one that is accessible in various ways. For example, we open a Facebook account by typing password and username because Facebook has made a database for accounts. Enter into database means that full access to a database by unauthorized access.
R – Return Anonymous
Return anonymous means that Go back without getting any hint to the victim.
Thank you Harinderpreet !
You explained each forms very well, I appreciate your effort. Good Luck Brother.
Good talk about Hacker. Its a great expansion and this is a work that needs to be appreciated .
It doesn’t need any alteration it is simply enough for who wants to know about hackers and hacking…
thank you very much
its difficult to find complete information but with this website i can find complete information about hacking. after reading full form of hacking its very easy to understand what is hacking and even i can find my system and ph`s ip address.thanksss
Thank you for your words